Database
Turn On BitLocker for Fixed Drives in Windows 10
For extra protection, Windows 10 allows enabling BitLocker for fixed drives (drive partitions and internal storage devices). It supports protection with a smart card or password. You can also make the drive to automatically unlock when you sign in to your user account.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
BitLocker was first introduced in Windows Vista and still exists in Windows 10. It was implemented exclusively for Windows and has no official support in alternative operating systems. BitLocker can utilize your PC's Trusted Platform Module (TPM) to store its encryption key secrets. In modern versions of Windows such as Windows 8.1 and Windows 10, BitLocker supports hardware-accelerated encryption if certain requirements are met (the drive has to support it, Secure Boot must be on and many other requirements). Without hardware encryption, BitLocker switches to software-based encryption so there is a dip in your drive's performance. BitLocker in Windows 10 supports a number of encryption methods, and supports changing a cipher strength.
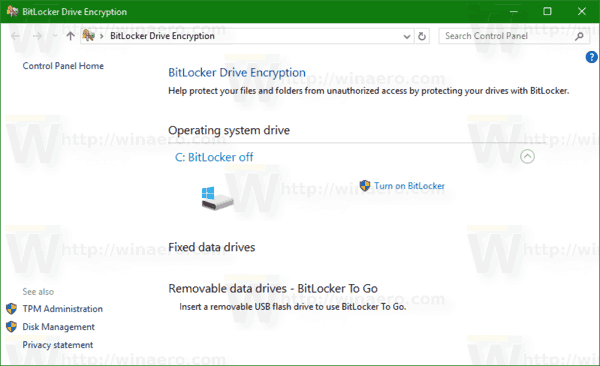
Note: In Windows 10, BitLocker Drive Encryption is only available in the Pro, Enterprise, and Education editions. BitLocker can encrypt the system drive (the drive Windows is installed on), and internal hard drives. The BitLocker To Go feature allows protecting files stored on a removable drives, such as a USB flash drive.
There are a number of methods you can use to turn on or off BitLocker for an internal fixed drive.
To Turn On BitLocker for a Fixed Data Drive in Windows 10,
- Configure the encryption method for BitLocker if required.
- Open File Explorer to the This PC folder.
- Right-click on the drive and select Turn on Bitlocker from the context menu.
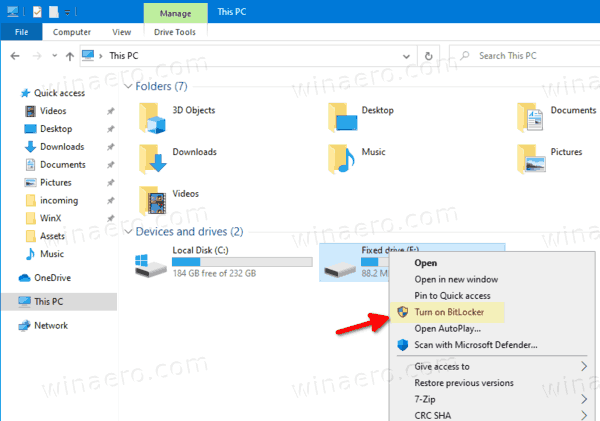
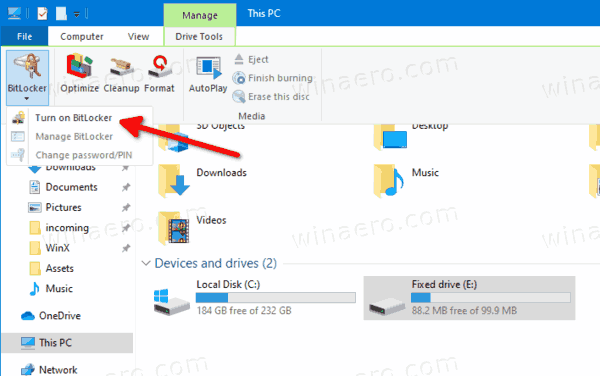
- Alternatively, click on Manage tab under Drive Tools in the Ribbon, then click on the Turn on BitLocker command.
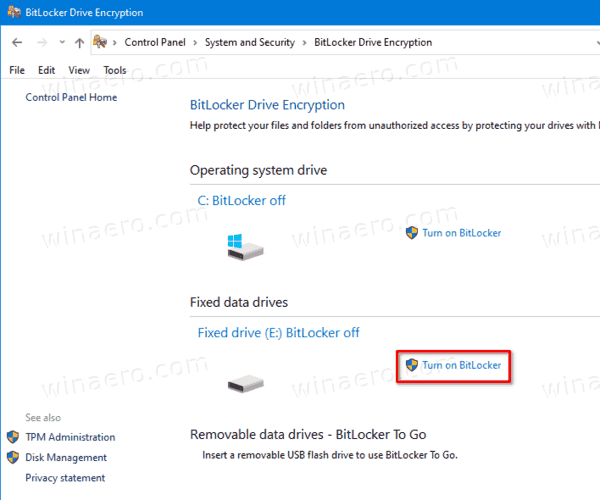
- Finally, you can open Control Panel\System and Security\BitLocker Drive Encryption. On the right, find your internal drive or partition, and click on the link Turn on Bitlocker.
- In the next dialog, choose a smart card or provide a password to encrypt the drive contents.
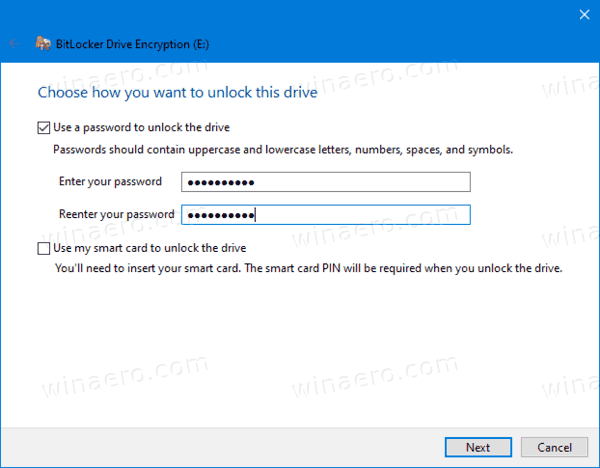
- Choose how to backup the encryption key. For example, you can print it.
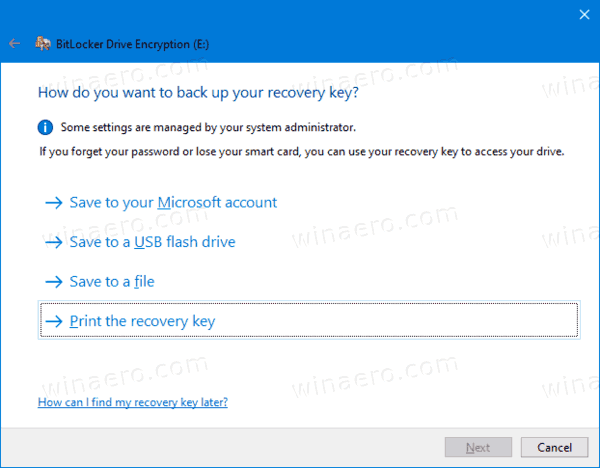
- Select how much of your drive space to encrypt. For new drives, you can choose 'used disk space only'. For drives that already contain files, choose Encrypt entire drive.
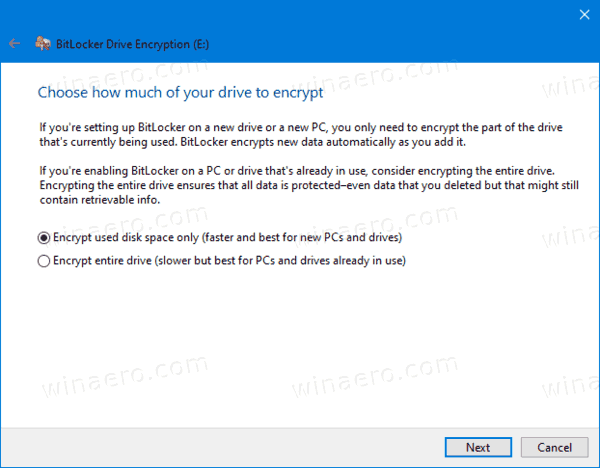
- Specify which encryption mode to use.
- New encryption mode (XTS-AES 128-bit) is supported on Windows 10.
- Compatible mode (AES-CBC 128-bit) is supported on Windows Vista, Windows 7 and Windows 8/8.1.
- Click on Start encrypting.
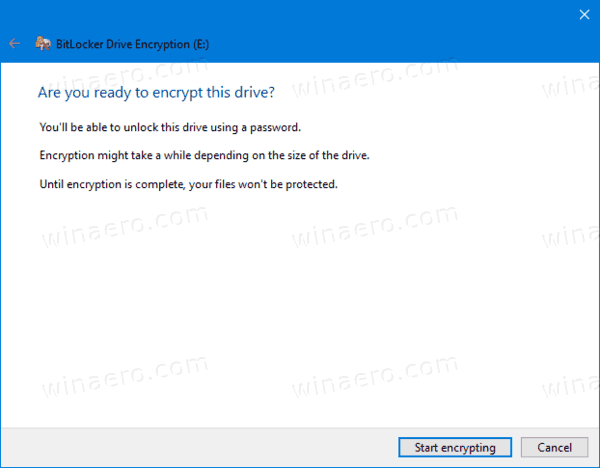
You are done. The fixed drive will be encrypted. This could take a long time to finish depending on the data size stored on the drive, and its capacity.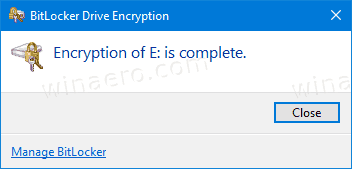
You can now check the BitLocker encryption status for the drive.
To Turn Off BitLocker for a Fixed Drive in Windows 10,
- Open File Explorer to the This PC folder.
- Right-click on the drive and select Manage BitLocker from the context menu.
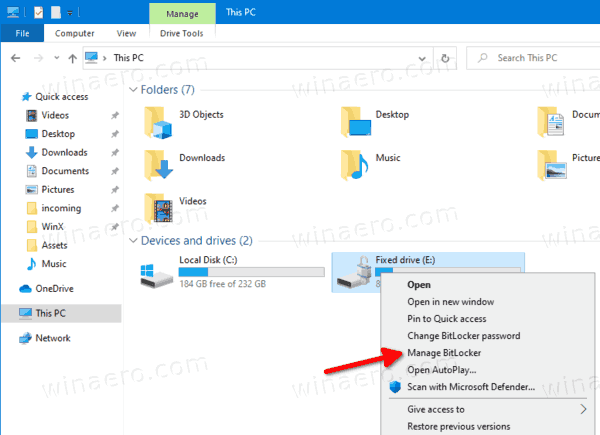
- Alternatively, click on Manage tab under Drive Tools in the Ribbon, then click on the Manage BitLocker command.

- Finally, you can open Control Panel\System and Security\BitLocker Drive Encryption.
- On the right side of the Drive Encryption Dialog, find your fixed drive, and click on the link Turn off BitLocker.
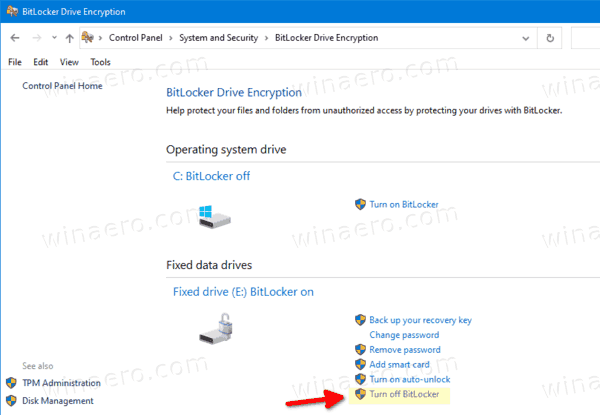
- Click on the Turn off BitLocker to confirm the operation.
You are done. BitLocker will decrypting the drive contents.
You can now check the BitLocker encryption status for the drive.
Also, you can disable BitLocker for an internal drive from Command Prompt or PowerShell.
To Turn Off BitLocker for a Fixed Drive from the Command Line
- Open a new command prompt as Administrator.
- Type and run the following command:
manage-bde -off <drive letter>:. - Substitute
<drive letter>with the actual drive letter of the drive you want to decrypt. For example:manage-bde -off D:.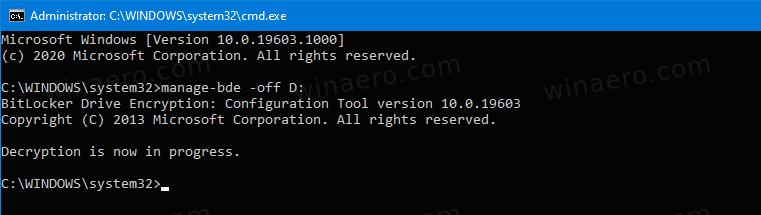
- Alternatively, open PowerShell as Administrator.
- Type and run the following command:
Disable-BitLocker -MountPoint "<drive letter>:". - Substitute
<drive letter>with the actual drive letter of the drive you want to decrypt. For example:Disable-BitLocker -MountPoint "D:".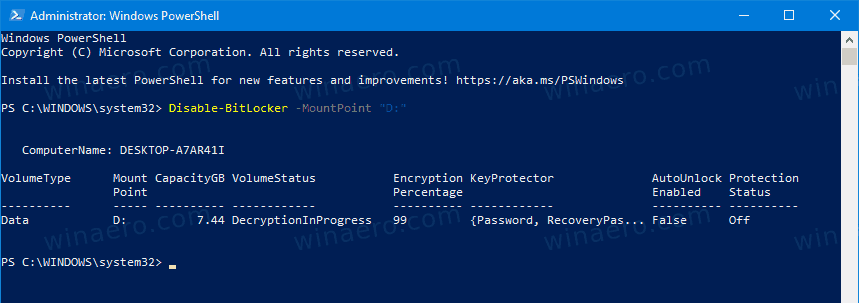
You are done!
Source: https://winaero.com/blog/turn-on-bitlocker-for-fixed-drives-in-windows-10/
'Access denied; you need (at least one of) the PROCESS privilege(s) for this operation' when trying to dump tablespaces
I am trying to backup mysql using the command
mysqldump -u root -p database_name > backup.sqlbut it is throwing an error:
'Access denied; you need (at least one of) the PROCESS privilege(s) for this operation' when trying to dump tablespaces
Also, i wanted to make a backup my database with all tables saperately sotored as a file. How can i do it?
Solution:
use --no-tablespaces
Sticky Password Review
Quick Summary
If every password is a key, I feel like a jailor. The weight of that huge keychain weighs me down more and more every day. It’s hard just to remember them all, but I’m also meant to make them hard to guess, different on every website, and change them all at least yearly! Sometimes I’m tempted just to use the same password for every website and be done with it! But that’s a very bad idea. Use a password manager instead.
Sticky Password is available for Windows, Mac, Android, and iOS, and works with a wide variety of web browsers. It automatically fills in online forms, generates strong passwords, and automatically logs you into the websites you visit. It’s less expensive than its main competitors yet the Windows app offers a similar number of features.
But there are some negatives. Unfortunately, the app looks a little dated, the Mac app is missing some important features, and the web interface offers little functionality. Why would you choose Sticky Password over its competitors? It offers two unique features that might appeal to you:
- Sync over a local network. If you’d rather not keep your passwords on the internet but still want them available on every device you own, Sticky Password is the best app for you. Its “no-cloud wifi sync” can synchronize your passwords between devices without storing them in the cloud. I’m not aware of any other app that can do this.
- Lifetime plan. If you’re sick of subscriptions and would rather just pay for the program outright, Sticky Passwords offers a Lifetime plan (see below). Buy it, and you’ll never pay again. It’s the only password manager I know of that offers this.
How much does it cost? For individuals, three plans are offered:
- Free plan. This offers all the features of the Premium plan to one person on one computer and includes a 30-day trial of Premium. It doesn’t include sync, backup and password sharing, so it won’t be a good long-term solution for most people, who own multiple devices.
- Premium plan ($29.99/year). This plan offers every feature and will sync your passwords to all of your devices.
- Lifetime plan ($199.99). Avoid subscriptions by purchasing the software outright. It’s equivalent to almost seven years of subscriptions, so you’ll have to use it long-term to make your money back.
- Plans are also available for Teams ($29.99/user/year) and Academics ($12.95/user/year).
New Update: Sticky Password kindly offers SoftwareHow readers an exclusive 50% off discount for both Premium and Lifetime plans, get this limited time offer here.
What is two-factor authentication?
How Does Two-Factor Authentication Work?
When two-factor authentication is enabled, you must go through a second authentication process once you enter your username and password. Depending on how 2FA is set up, you may have to verify your identity using one of the following methods:
- Something you know such as your mother’s maiden name or a personal identification number;
- Something you have like your smartphone or credit card;
- Something you are such as a scan of your fingerprint or the iris of your eye.
Two-factor authentication is more secure because even if your password has been compromised, there’s a good chance the hacker won’t have the second piece of information needed to complete the authentication process. For example, if a website is set up to send a code to your smartphone as the second form of authentication, there’s a good chance the hacker won’t have your smartphone in his or her possession. Therefore, the authentication will fail, preventing an unauthorized user from gaining access to your account.
The use of two-factor authentication helps users avoid the consequences of several password-related problems. Many people now have dozens of online accounts, making it difficult to remember the password to each one. As a result, some people write down their passwords, increasing the risk that an unauthorized individual will be able to access a private account. Password recycling is also a common problem. This occurs when people use the same password for multiple accounts. Hackers take advantage of password recycling by testing stolen usernames and passwords against popular websites. If you use the same username and password for multiple sites, the hacker will be able to use your stolen credentials from one site to log in to multiple accounts.
Types of Two-Factor Authentication
Biometrics
Biometric authentication is one of the most secure forms of 2FA because it relies on something you are. It’s very unlikely that a hacker will be able to capture your fingerprints or voice, and the technology is so new that hackers haven’t had a chance to develop effective methods of bypassing it. Another reason biometric authentication is so secure is because fingerprints, voice prints, hand shape, and other accepted forms of authentication contain many data points. Even if a hacker could replicate one point, it would be extremely difficult to replicate them all. When used by corporations, biometric authentication also reduces costs by eliminating the need for key cards and security passes.
Push Notifications
Push notifications alert you when someone is trying to access one of your accounts. If a website uses push notifications, you’ll receive a notification on your smartphone or other device every time you attempt to log in. When the notification pops up, you’ll be able to approve it immediately, reducing the amount of time it takes to access your account. If an unauthorized person attempts to log in, you’ll be able to deny the attempt. One of the main drawbacks of this type of 2FA is that you may have difficulty receiving the notifications if you’re in an area with a poor internet connection.
SMS Messages or Voice-Based Authentication
SMS and voice-based authentication use your smartphone to control access to your online accounts. For sites using SMS authentication, you enter your username and password as usual. Then, the website sends you a text-message containing a one-time passcode that can be used to complete the second step of the authentication process. Voice-based authentication works much the same way. Instead of sending you a one-time passcode via SMS message, the website automatically calls your smartphone. When you answer the call, you receive a one-time passcode from the automated voice system.
Software Tokens
Software tokens are an alternative to SMS and voice-based authentication. Instead of receiving a one-time passcode via text message or phone call, you must download and install a 2FA application on your computer or mobile device. After entering your username and password, you must check the 2FA application and enter the code that appears. In many cases, the code is valid for only a minute; if you don’t enter it within the allotted time, you’ll need to generate a new code to access the website. A major advantage of using software tokens is that there’s a reduced risk of passcode interception because you use just one device to generate and display the code.
Websites and Apps That Use Two-Factor Authentication
Although many websites still rely on usernames and passwords, two-factor authentication isn’t a new form of technology. In fact, the chip-and-pin technology used to prevent the unauthorized use of debit and credit cards was developed nearly two decades ago. Since then, companies in many industries have implemented two-factor authentication to make their sites more secure. These industries include banking, education, finance, entertainment, gaming, and retail. Several major companies, including Facebook and Google, now offer two-factor authentication to protect your personal information. All you have to do is log in to your account and enable 2FA.
Source: https://www.passwordmanager.com/what-is-two-factor-authentication/
Date of publication
Filter by category
Search Post
About CNERIS
CNERIS is a company formed by young entrepreneurs from different sectors of the world of information. Our team consists of programmers, system administrators, graphic designers.



