Web development
CNERIS.COM
Script for detecting proxy and VPN
$proxy_headers = array(
'HTTP_VIA',
'HTTP_X_FORWARDED_FOR',
'HTTP_FORWARDED_FOR',
'HTTP_X_FORWARDED',
'HTTP_FORWARDED',
'HTTP_CLIENT_IP',
'HTTP_FORWARDED_FOR_IP',
'VIA',
'X_FORWARDED_FOR',
'FORWARDED_FOR',
'X_FORWARDED',
'FORWARDED',
'CLIENT_IP',
'FORWARDED_FOR_IP',
'HTTP_PROXY_CONNECTION'
);
foreach($proxy_headers as $x){
if (isset($_SERVER[$x])) die("You are using a proxy!");
}How to Build an eCommerce Website
According to survey reports, the growth of online business worldwide is significantly faster and higher as compared to traditional businesses. The success of online commerce has been so impacting that even established business houses have started online selling as a complementary effort. However, first things always come first, and in case of eCommerce, it is mandatory to create an eCommerce website at the outset.
There is a definite way of going about the process of creating and operating an eCommerce website. Though a professional involvement is always solicited for such efforts, a fair knowledge could also help in initiating an online business.
Follow these steps to build your eCommerce store
Decide the Product You Want to Sell
While browsing the internet you must have noticed the existence of multiple eCommerce websites selling varied items. There are certain websites dedicated to selling a particular line of products or services such as garments, travel plans, fashion items, etc. Also, there are some other eCommerce websites that sell multiple items like mobile phones, laptops, household appliances, books, CDs, home theatres, handy cams, sports goods, and so on. The latter is a like a huge departmental store selling everything under the same roof.
At the outset, it is thus important to decide on the product or service that you would like to sell through your website. While deciding on the item of trade it is essential to estimate the local demand. Buyers would always prefer to buy items from a local vendor irrespective of being online or offline. The local supplier would always ensure faster deliveries, easier payment terms, and earlier replacements in case of wrong or defective shipments.
Choose Your Business Model
As an eCommerce business owner, you can choose your business model as per your requirement. Either you can sell only through your online store, or, can sell your products on marketplaces like Amazon, FlipKart, eBay, etc. You can also sell your products on both the platforms at a time.
Choose a Business and Domain Name
Once you have decided on your range of items and business model, the next step would be to choose a business name and create a domain. A business name should be relevant to your products and easy to remember for your target audience. A domain gives an identity and makes it easier for online buyers to recognize you. However, for companies with limited financial resources, it would be desirable to get a shared domain. Sharing a domain with an established name makes it easier for reaching out to your target buyers. As the business grows it would be wise to have a dedicated domain as it helps in search engine optimization and easier recognition.
Select an eCommerce Website Builder
Nowadays, it’s very simple to build your online store with the help of eCommerce website builders like KartRocket. These DIY online software create websites in few seconds where you can start selling products instantly.
Designing Your eCommerce Store
Your eCommerce website is your store, and it needs to be designed for the convenience of your buyers. As in a store, your website should contain details about your saleable products and services. Images, descriptions, prices, users’ comments, ratings should all be included in your web page for guiding prospective buyers. You must make it certain, that your web page showcases your products perfectly so that buyers are never misled. You must make your web pages and website attractive as that is your representation to buyers online.
Set Up the Payment Gateway
As an online business, one must have multiple payment options available for the customers. The eStore builders like KartRocket come with tools that can set up these functionalities to your website automatically. The customer should be able to make payments via credit card, debit card, online wallets, net banking, COD, etc.
Secure Your Website by Installing SSL Certificate
For all the websites that transfer data online, one must make sure that their connection is protected by a secured security layer (SSL). The SSL certificate keeps your website secure and builds the trust among your customers. Nowadays, even Google recommends having an SSL certificate for every single website.
Select Your Shipping Partner
Once you start selling products through your eCommerce website, you need to ship those products to your customers with the help of courier services. eCommerce logistics aggregator services like ShipRocket are the best option to go for. They give you multiple courier agency options to ship your product with the lowest available shipping charges, so you may have maximum profit value in your share.
These are the basic steps in creating an eCommerce website for your product or service and start selling instantly.
Data security vs. network security: What should your business prioritize?
Many businesses that have allowed employees to continue working from home for the foreseeable future are aware that they need to update their cybersecurity. It’s likely that they have allocated some budget and IT resources to make those necessary changes. However, IT budgets are finite. Given the economic disruption of the pandemic, enterprises must strategically decide where to invest their cybersecurity budget most effectively.
There are many different approaches to cybersecurity, and the way your business previously protected data may no longer work in a remote-work paradigm. Here’s how to understand how working from home impacts your data security – as well as some steps to take to make sure you are prioritizing the right things.
Types of cybersecurity
Cybersecurity can be broken out into categories based on what you wish to protect. Cybersecurity practices are commonly classified into one of these five areas:
-
Network or perimeter security: protection for your network traffic by controlling incoming and outgoing connections. This prevents hackers and malware from entering and spreading throughout a network.
-
Data security or data loss prevention (DLP): protection for your data by enforcing strict protocols and safety measures on the location, classification and monitoring of data (both stored data and data as it is used).
-
Cloud security: protection for data used in cloud-based services and applications.
-
Device security: protection for on-premises devices such as computers and servers.
-
Application security: protection for your apps from attacks with testing, app shielding strategies, and more.
There are many subcategories within these broad cybersecurity distinctions, but IT professionals tend to focus on these areas.
All these types of cybersecurity are important. When offices are working business as usual, most IT professionals tend to prioritize network security first; devices, applications, and data sharing are all linked through the same network, so protecting the perimeter makes sense.
As more people work remotely, however, investing in network security makes less sense. Data protection and cloud security are more important as our online needs are rapidly changing. With limited investment available, how should you prioritize your cybersecurity?
New approaches to cybersecurity
As one expert reported in Forbes, “To protect customers, employees, and reputations while ensuring compliance with evolving regulations, companies should shift their security strategies from an outdated reliance primarily on ‘perimeter protection’ to a companywide approach based on ‘secure data access.’”
As our online behavior changes, the threats evolve too. Cloud services, for instance, are becoming a new target for hackers. McAfee found that remote attacks on cloud services and collaboration tools, like Slack, increased 630% during the first four months of 2020. Employees are using their own devices and their own networks, so shifting your cybersecurity to focus on cloud security is a good first step to protecting data outside the office firewall.
Data loss prevention, DLP, is another key area for IT professionals. Your enterprise must prioritize building a strategy that prevents unauthorized access to and use of data. There are three key areas here to consider:
-
Data discovery: measures to identify PII and other sensitive data as it is collected and used across your organization.
-
Data transformation: measures to secure data by masking or anonymizing PII so only those in the company who need access to data have it.
-
Data access: granular controls that ensure the right people can access specific data or data formats – role-based and attribute-based measures.
In the immediate term, IT professionals need to ramp up cloud security and data security to accommodate remote employees. Here’s how to do it.
Steps to improve your data security
One of the easiest ways to improve your data security is by educating your employees. This effort takes time, but very little financial investment.
Teach your team ways they can improve their at-home security practices. Nightfall found that lax email policies contribute to a huge amount of data theft. Poor password hygiene for email accounts – like using “password1234” or another easily guessable code – is a big mistake that many people are (still) making. Companies are also not utilizing multi-factor authentication when signing into accounts. Lack of employee training and clear WFH security policies are further contributing factors to the increase in data theft via email.
Next, address changes to your network security by providing tools for employees to safeguard their personal devices. One study by Security Magazine discovered that 56% of employees are using their personal computers to work remotely in response to COVID-19. Moreover, nearly 25% of employees working from home don’t know what security protocols are in place on their device. IT teams should perform one-on-one audits with each remote worker to assess what security measures are in place and provide the tools and feedback needed to improve the cybersecurity of at-home networks and devices.
Lastly, add an automated DLP solution like Nightfall to dramatically improve your data security.
About Nightfall
Nightfall is the industry’s first cloud-native DLP platform that discovers, classifies, and protects data via machine learning. Nightfall is designed to work with popular SaaS applications like Slack & GitHub as well as IaaS platforms like AWS. You can schedule a demo with us below to see the Nightfall platform in action.
“This article is originally posted on Nightfall.ai”
Known Vulnerabilities Scanner
The SafetyDetectives vulnerability tool is the only free online scanner that quickly checks your PC and devices for known vulnerabilities (CVE Database). Once the scan is complete, it will explain how to fix any issues that may have been detected.
1. What does this vulnerability scanner do?
This online tool works with the Common Vulnerabilities and Exposures (CVE) database to make sure your software is updated with the latest security patches.
The CVE database contains the world’s largest database of cybersecurity vulnerabilities. When IT professionals find and fix a vulnerability issue within a program, they report it to the CVE database so that all users can keep their software up-to-date.
The SafetyDetectives vulnerability tool scans your operating system’s settings and browser against the information in the CVE database, and it recommends security patches based on those vulnerabilities.
2. How do I know if my computer is infected with a virus?
Classic symptoms of a virus are:
- Computer freezes
- Slow performance
- Popup error messages
- Application crashes
Many cybercriminals create viruses which run silently in the background — stealing credit card numbers, bank account passwords, and other private data without you even knowing. It’s possible that you might not even experience any of these “classic virus symptoms”.
While online tools like this one can help identify software security flaws, they are unable to detect and remove viruses from a computer system. For that, you’ll need an antivirus program.
3. How do I get rid of malware?
If you know your computer has malware on it, you’ll need to download an antivirus scanner — like Norton or McAfee. These programs will detect and remove all of the malware from a system, and they’ll guarantee that you stay protected against all future threats.
4. What's the best way to stay protected from malware?
The first thing you should do is learn the basics of how to keep your computer secure (Mac users go here; Windows 10 users go here).
This means that you need to have an antivirus installed, you need to stay away from dangerous websites, and you need to stay up-to-date with the latest security patches for both your OS and your system’s applications.
5. Do I need to pay for an antivirus?
When it comes to antivirus software, you get what you pay for! No business model supports “free” products — you’re always going to “pay” somehow.
Most internet security companies which have free antivirus software only provide very basic protection to their free users. They’ll eventually ask for you to pay for an upgrade before they’ll provide you with complete antivirus coverage. Some companies — like Avast/AVG — might even steal your browsing data and sell it to advertisers as compensation for providing a free product.
That said, there are some decent antivirus programs available for free. But free antiviruses should only be used to secure systems that don’t have a lot of sensitive information — passwords, banking info, photos/videos, etc. It’s always best to not deal with the limitations of a free antivirus and instead download a low-cost premium antivirus like Norton 360.
Source: https://www.safetydetectives.com/vulnerability-tool/
How to choose the best VPN
For those new to the world of VPNs, getting started can seem a little overwhelming. With so many paid and free options available, it’s not always easy to find the right fit for individual needs. This is what you need to know to choose the right VPN for you, no matter why you want a VPN or what you are trying to accomplish.
What to Look for When Picking a VPN
There are a number of factors that go into choosing an appropriate VPN. Some of these elements are recommended for all VPN users while others may be a matter of personal preference. From safety to server location, there are plenty of things to keep in mind when weighing the pros and cons of different VPN services.
Privacy and security are top priorities.
For many, the main driver behind choosing to use a VPN is addressing privacy and security concerns. By encrypting data transmission and masking identifying information, using a VPN can make web use safer, easier, and more private.
However, not all VPNs offer the same level of security and protection. When choosing VPN options, it’s important to evaluate things like encryption keys to ensure protection is adequate. For example, some VPNs use 128 bits or even 256-bit strings to make encryption virtually impenetrable, while others employ ciphers like Blowfish, Twofish, and AES. By knowing what these terms mean and how they apply to safety, users can ensure the VPN they select can properly protect personal information and data transmissions.
Consider the cost and be wary of free options.
VPN costs can vary from free to around $30 per month for personal use models; corporate products can cost significantly more. Pricing often varies based on things like security measures and servers available. VPNs that can accommodate things like streaming and gaming can be more expensive, and those that prioritize basic functionality are more affordable.
There are free products on the market, but some free VPNs can be more problematic than beneficial. Some free products contain malware while others lack the security necessary to keep your devices protected. Even the FBI warns against free VPNs, so if at all possible, stick with paid options that provide trusted services and proven security.
Server accessibility and locations.
Server location can affect what sites and services are accessible; many sites, particularly streaming platforms like Netflix and Hulu, have geographical restrictions. Before choosing a server, VPN users should be sure there are adequate servers available in their chosen locales. In general, a single server isn’t enough. Should something go wrong with one option, having others available can be critical. For example, U.S.-based web users who want to ensure all U.S.-specific sites and services are available when using a VPN should select a product with a focus on domestic servers versus one with a strong overseas presence.
Determine performance parameters.
VPN performance can also differ in a few ways from one product to another, including things like speed, device compatibility, and data limitations. Before choosing a VPN, it’s important to know the specifications surrounding performance. Some VPNs do things like limit the amount of data that can be used or offer membership tiers that restrict use to a single device without an increased monthly fee.
The extent to which performance matters can be a personal issue. Web users who require a fast connection to do things like stream media or play online games, for example, are encouraged to choose a VPN that can meet these needs.
Choose the right connection protocols.
A VPN, in essence, creates a tunnel between public networks and a private one. This is the basis for the security that can be provided. However, not all VPNs do this in the same way. The connection protocols in use, which include options like PPTP, L2TP and SSTP, can affect things like how data is routed and the security of a connection. The wrong connection protocol may negatively affect use, so understanding how VPNs connect and why can be valuable criteria to assess in the selection process.
Why Do You Need a VPN?
There are several reasons why a web user may feel they need a VPN, including functionality that goes above and beyond securing data transmission.
For many individual web users, VPNs are most commonly selected to hide movements online or prevent the chances of cyber attack through an unsecured network. However, others may choose a VPN to hide activity like torrenting from an ISP, access web content that is restricted based on location and improve lag times and ping when gaming by using a faster server connection.
Businesses that employ VPNs may have other priorities. In a corporate setting, VPNs are often used to let users access a business network remotely. This prevents the likelihood of an information breach while giving employees the flexibility to work outside of a company’s physical location.
The reason for choosing a VPN is by and large a personal one. Some web users feel the protection provided by their own network or anti-virus software is adequate and are not concerned about additional security while others are highly concerned with privacy and protection.
What Is a VPN?
A VPN is a virtual private network or a tool that encrypts data transmission to protect against attack and the release of identifying information. By shielding your information and providing a secure way to transmit data, a VPN offers privacy and protection in an easy-to-use, affordable manner.
Normally, your computer uses the connection provided by your internet service provider, or the provider of any network you may be using, to send and receive data. A VPN circumvents this, creating a tunnel between your personal connection and a private network that shields the information available about your network and device. By essentially replacing this connection with that of a server located elsewhere, VPN users can hide identifying details about devices and networks and create a secure connection that reduces the likelihood of a data breach.
How Does a VPN Work?
A VPN is a virtual connection created between a device and the internet. Instead of connecting directly to a network like normal, a VPN creates an encrypted virtual tunnel that adds an extra layer of security to web use.
Usually, a web-enabled device uses the connection provided by a personal internet service provider, or ISP. However, doing this essentially tags your device with the information provided by this connection, also known as an IP address. IP addresses are effectively pieces of identifying information unique to each internet connection point, much like a phone number or address. This means that the information associated with your IP address is communicated to every site you visit or email you send. However, using a VPN will route your standard internet connection through a secure, encrypted alternative, displaying a different IP address and making it much harder for anyone to track your online activity or breach your device through data transmissions.
VPNs can be used to hide data anywhere but can be most effective on unsecured networks, like public networks available in retail stores or restaurants where the risk of use is much higher.
Source: https://www.vpnratings.com/how-to-choose-the-best-vpn/
How does a VPN work?
The Basics
Each time you connect to the internet using your computer, tablet or smartphone, if you’re using a VPN, it connects you to another computer, called a server. This server can be in one of several locations in one of several countries, depending on how many server connections a VPN has in its arsenal. As you browse the web or work online, everything you do is sent over this secure connection and routed through the server’s internet connection and an encrypted virtual tunnel. Thus, any data you send to a website and any data that comes back to you from the website all goes through this secure connection, masking and protecting your information and online identity.
By encrypting your data and making your IP address and location invisible, a VPN helps protect you from hackers and cybercriminals looking to track what you’re doing online and/or steal your personal information. This can be especially important when you’re using public Wi-Fi connections that aren’t very secure. A VPN effectively shields your browsing activity from everyone, but you can also use it to gain access to websites that restrict users from certain regions. When you browse the internet using a VPN connection, your IP address changes and makes it appear as if you’re browsing from the location/country of the VPN server, instead of where you really are. This helps you gain access to websites or online services blocked to certain geographical locations.
Downloading and installing a VPN is as easy as any other app, and it’s one of the simplest ways to protect your privacy online. Good VPNs can be set up instantly without any complicated steps using the in-app instructions and are also easy to use. Once installed, all you do is connect to a server of your choice when you go online and disconnect when you’re done. The VPN does all the rest while you confidently surf the Internet knowing your information and web activity are being guarded.
How to Pick the Best VPN
There are tons of VPN providers out there to choose from with distinct advantages and disadvantages, so there isn’t a single service that’s perfect for everyone. There are several important features to consider when choosing the best VPN for your needs.
Security/Privacy. All VPN companies say they don’t save your connection logs or what you’re doing online, but sometimes data collection occurs. Always check the Privacy Policy and Terms of Service to learn exactly what’s collected and how long it’s kept and to ensure they never sell your information. For the most privacy, choose a VPN that operates under a no-logs policy, meaning your connection and bandwidth data will never be collected, stored, or shared.
Location & Servers. A large server list spread out over multiple countries is an integral part of any good VPN service. The VPN should have servers available in the geographical locations you need with numerous servers available in each country or region to spread out the load of multiple users to guarantee optimum performance all the time.
Performance. Check important performance features, such as how many devices you can have connected simultaneously, download speeds and monthly data limits, which can all affect your streaming capabilities — especially if multiple household members use the same connection. On average, VPNs allow between three and seven devices to be connected at the same time, but this number varies between one and unlimited.
Cost. Like any service, beware of cheap or free plans that may restrict features or only offer discounts for the first billing period then automatically renew at much higher pricing. Always read the fine print on the pricing details, and if the service renews automatically, choose a payment option that lets you easily cancel subscriptions yourself.
Why Do You Need a VPN?
VPNs were originally created to provide businesses with a way to securely connect their networks together over the internet and allow employees to access the business’ network while working off-site at home, on the road, or abroad. While businesses still use VPNs for these reasons, individuals seeking safer internet access also found many other reasons why they need a VPN, including:
- Online anonymity through a hidden IP address and location
- Increased online security, especially while using public networks or Wi-Fi hotspots
- Accessing a home or business network while traveling
- Safe, anonymous downloading and uploading of files
- Ensuring emails and instant messages remain private
- Hiding browsing activity from a local network and internet service provider
- Bypassing restrictions based on geography or censorship, such as streaming services, social networking or internet content not available in every country
- Protection from hackers who intercept and steal data unknowingly spread while browsing the web
- Blocking advertising networks from collecting information about you to sell to third parties
- Preventing slower internet speeds when your internet service provider throttles down your service due to using a lot of bandwidth while streaming or downloading large files
How Much Does a VPN Cost?
With so many VPN services available, you’ll find a huge price range. The costs for a VPN also vary greatly based on the features you want, so make sure you understand what you’re getting for the price. However, a good VPN usually isn’t very expensive, with most costing less than $10 per month. Premium plans with additional security or encryption typically increase your cost, but these plans may be worth it, depending on your needs.
There are also free VPNs available and some companies with paid-for services that offer a basic service that don’t cost anything. Like most free products, these no-cost services typically come with several catches. The most common drawbacks are data caps, session limits, usage restrictions, and advertising. Many free VPNs aren’t reliable and don’t secure your connection nearly as well as paid services. Untrustworthy free VPN services may even install malware on your devices. However, you can find good free VPN services that may be fine for protecting your laptop during infrequent public Wi-Fi usage, but commercial products are still the better choice.
Most VPNs offer a per-month fee as part of a subscription with varying lengths of commitment available. The longer your subscription, the less you’ll pay in the long run. Some VPNs also offer deeper discounts on service plans when you opt to pay for a couple of years up front. Before you spend a lot of money, it’s advisable to pay for only a month first. If you’re still happy after this trial period, upgrade to a longer plan that offers a better value.
Source: https://www.vpnratings.com/how-does-a-vpn-work/
What is a VPN?
In an age when data breaches have become a universal challenge facing websites and networks of all sizes, affecting millions and sometimes even hundreds of millions of users at a time and costing business millions of dollars to address, internet privacy has become a more urgent issue than ever.
One of the most important developments in privacy, both for private individuals and businesses, has been the Virtual Private Network or VPN. VPNs are simple, elegant privacy solutions that make the internet safer for their users by making it harder for hackers and cybercriminals to compromise their systems and providing more anonymity and freedom while browsing. Here, we’ll provide an overview of VPNs, including how they work, what kinds of protection they provide and a typical range of costs.
How Does a VPN Work?
Every device, when connecting to the internet, has a unique address rather like a phone number or street address, but for the user’s smartphone, tablet, or computer. This is called an Internet Provider or IP address. It’s tied to whoever is paying for internet access at the user’s location, and it identifies exactly where that location is. In normal circumstances, without the use of encryption, the unique IP address associated with each login is public information, fairly easy to access for someone who knows how and just as easily used to recognize and trace someone’s online activity. That information, in turn, can be exploited for the purpose of hacking your computer, among other things.
Given the amount of time that many of us spend working, playing and doing business online and the volumes of personal information going out over many an internet connection, it’s more than understandable that you might not want just anyone to be able to look up your IP address. This is where Virtual Private Networks or VPNs come in. A VPN installs encryption software on your device that provides a secure connection to an external server, which sends traffic from your device to the internet. This arrangement is designed to hide your IP address from prying online eyes.
There are a few basic steps a VPN goes through to encrypt your data, transmit it to the internet and then have the internet transmit data back to you. VPN software, usually called a VPN client, first encrypts the data on the user’s device. The VPN client then sends the data to a VPN server, which decrypts it and sends the data to the internet, requesting a reply meant for the user. When the reply arrives, the VPN server encrypts the data again and forwards it to the user, and the VPN client on the device decrypts the data to make it usable.
It’s important to remember that while a VPN provides additional protection, it doesn’t totally guarantee anonymity.
A VPN provides the most security when you’re using it to connect to sites that use the modern secure hypertext protocol. That may sound a bit technical, but what it means is that if the site’s address in your browser starts with HTTPS instead of just HTTP, that site has been designed with extra security in mind. On an HTTPS site, your VPN will provide what’s called “end-to-end encryption,” fully protecting your anonymity at every step in transmitting information from your device to the host of the website you’re accessing. Fortunately, most of the Internet is converting to HTTPS as the new standard.
Web browsers can sometimes “leak” private information — for example, through automatically integrated plug-ins like WebGL and WebRTC, which are used to increase the efficiency of conferencing apps and programs like Skype, Discord and Google Hangouts — that can be used to identify your browser settings and profile your online activity. Some VPNs protect against this, but not all of them do. The good news is that this information isn’t nearly as easy to access or exploit for other people as simply leaving your IP address in public view, so in most cases, your VPN will still preserve your anonymity quite effectively. If you want to ensure that your security is at its best, it’s worthwhile to check for specific kinds of browser leaks and make sure that any VPN you’re considering can specifically address them.
Why Do You Need a VPN?
There are several ways in which keeping your IP address from public view can enhance the internet experience. A VPN provides better security, it offers more privacy and it enables more freedom of access to what the internet has to offer.
Better online security
The kind of security a VPN provides is on the way from being a luxury to becoming a necessity on the modern internet. While directly hacking a computer using its IP address is difficult today, thanks to the various firewalls employed by service providers, an IP address can still be used as a starting point to access location data that can then be used to dig up further sensitive information. What makes a VPN effective is that it encrypts your internet traffic before it reaches any server outside of your device. As that encrypted traffic passes through the steps described in the above section, which can be thought of as a kind of VPN tunnel, it becomes considerably more difficult for outside parties — including governments and hackers — to access your data and location.
Added privacy online
The location data provided by an IP address allows other people to link your identity and locale with your internet activity. When your address is publicly accessible, your internet provider and, often, governments or other online actors can see everything you do online. There are plenty of ways in which that information can be used to assemble a profile of you at a disconcerting level of detail. With a VPN, online activity can only be traced back to the VPN server, which won’t disclose and often does not track actions taken through the server.
More freedom of access
There are often restrictions on access to the internet that vary from one country to another, or restrictions on which content can be viewed from which country, that can limit a user’s ability to access certain sites online. Travelers might find themselves in a place where the internet is censored in various ways (“political” media and social media are common targets); or they may find they no longer have access to their favorite media streams at their current location for reasons other than censorship (Hulu isn’t normally viewable outside the United States or Japan, for instance). A VPN lets users connect to servers in any country as if physically present there.
How Much Does a VPN Cost?
The internet is awash in free services calling themselves VPNs. For the most part, these are best avoided. As per the old adage “you get what you pay for,” most of these services simply aren’t safe to use. An effective VPN is kept rigorously up to date by the people operating it, using the latest standards and best practices and patching potential vulnerabilities. Free services generally do not do this, and some of them get their bandwidth from inherently not secure peer-to-peer operating models.
Truly functional VPNs will typically come with at least some associated costs. It’s best to avoid locking yourself into a seemingly cheap “lifetime” contract with a VPN, as there’s no guarantee of the needed quality always being there, so a quality, secure VPN will typically involve some monthly or annual expense. Month-to-month pricing for the leading VPN services ranges from $5-$12. Annual pricing ranges from $35-$100 per year — sometimes this kind of pricing is structured as a biennial contract. Whatever the cost of truly quality VPN, it’s a worthwhile expense to enjoy true security, choice and privacy on today’s internet.
Source: https://www.vpnratings.com/what-is-a-vpn/
Turn On BitLocker for Fixed Drives in Windows 10
For extra protection, Windows 10 allows enabling BitLocker for fixed drives (drive partitions and internal storage devices). It supports protection with a smart card or password. You can also make the drive to automatically unlock when you sign in to your user account.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
BitLocker was first introduced in Windows Vista and still exists in Windows 10. It was implemented exclusively for Windows and has no official support in alternative operating systems. BitLocker can utilize your PC's Trusted Platform Module (TPM) to store its encryption key secrets. In modern versions of Windows such as Windows 8.1 and Windows 10, BitLocker supports hardware-accelerated encryption if certain requirements are met (the drive has to support it, Secure Boot must be on and many other requirements). Without hardware encryption, BitLocker switches to software-based encryption so there is a dip in your drive's performance. BitLocker in Windows 10 supports a number of encryption methods, and supports changing a cipher strength.
Note: In Windows 10, BitLocker Drive Encryption is only available in the Pro, Enterprise, and Education editions. BitLocker can encrypt the system drive (the drive Windows is installed on), and internal hard drives. The BitLocker To Go feature allows protecting files stored on a removable drives, such as a USB flash drive.
There are a number of methods you can use to turn on or off BitLocker for an internal fixed drive.
To Turn On BitLocker for a Fixed Data Drive in Windows 10,
- Configure the encryption method for BitLocker if required.
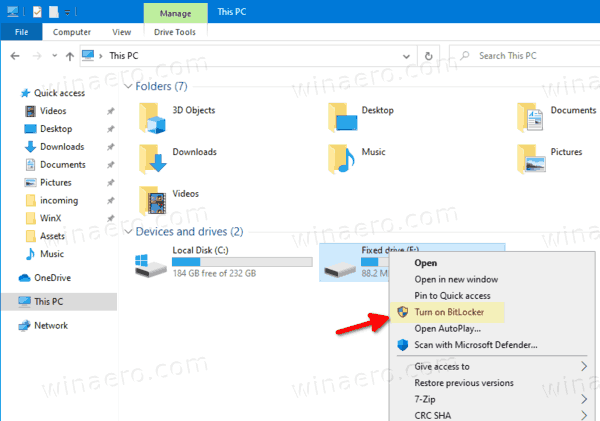
- Open File Explorer to the This PC folder.
- Right-click on the drive and select Turn on Bitlocker from the context menu.
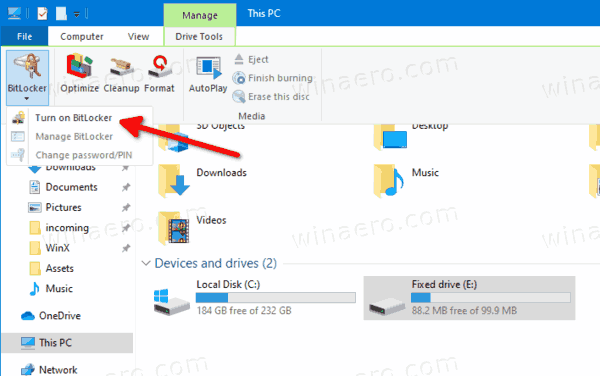
- Alternatively, click on Manage tab under Drive Tools in the Ribbon, then click on the Turn on BitLocker command.
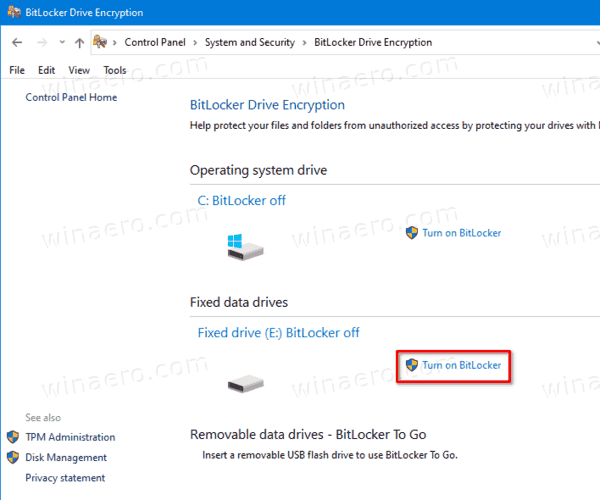
- Finally, you can open Control Panel\System and Security\BitLocker Drive Encryption. On the right, find your internal drive or partition, and click on the link Turn on Bitlocker.
- In the next dialog, choose a smart card or provide a password to encrypt the drive contents.
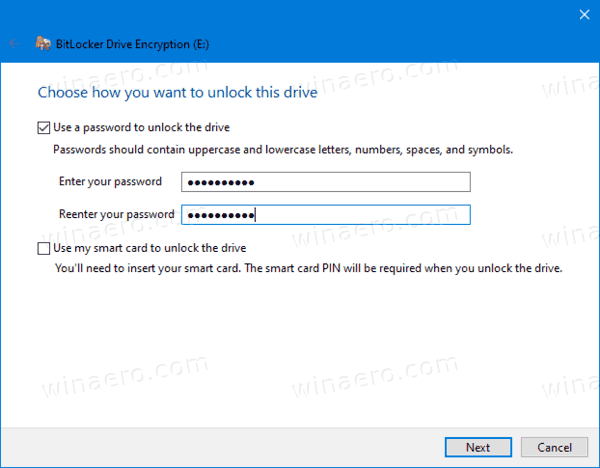
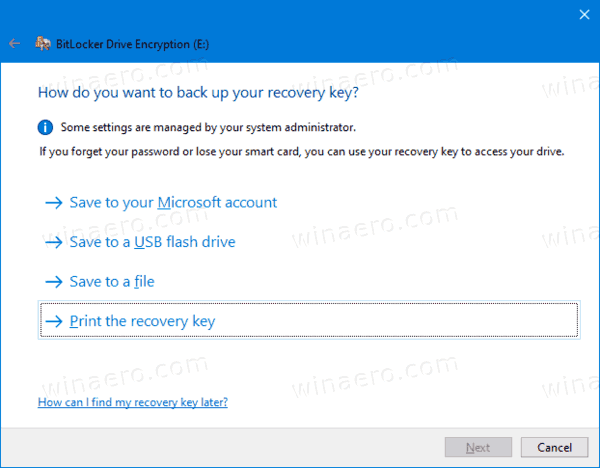
- Choose how to backup the encryption key. For example, you can print it.
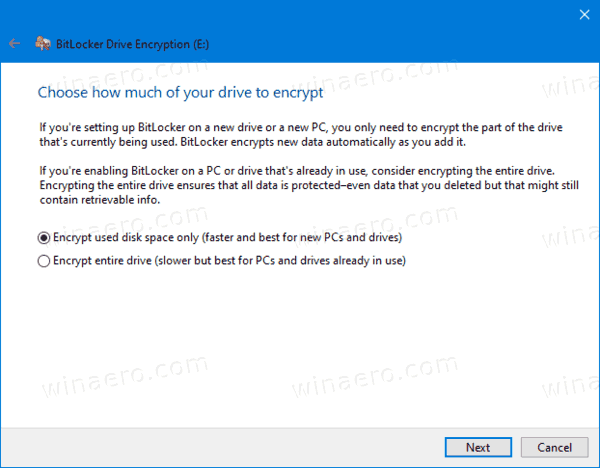
- Select how much of your drive space to encrypt. For new drives, you can choose 'used disk space only'. For drives that already contain files, choose Encrypt entire drive.
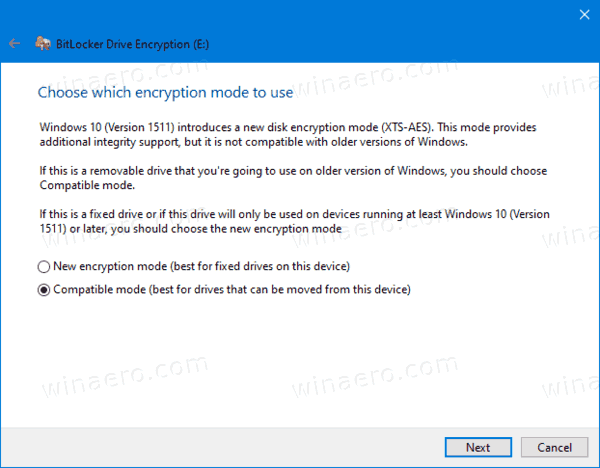
- Specify which encryption mode to use.
- New encryption mode (XTS-AES 128-bit) is supported on Windows 10.
- Compatible mode (AES-CBC 128-bit) is supported on Windows Vista, Windows 7 and Windows 8/8.1.
- Click on Start encrypting.
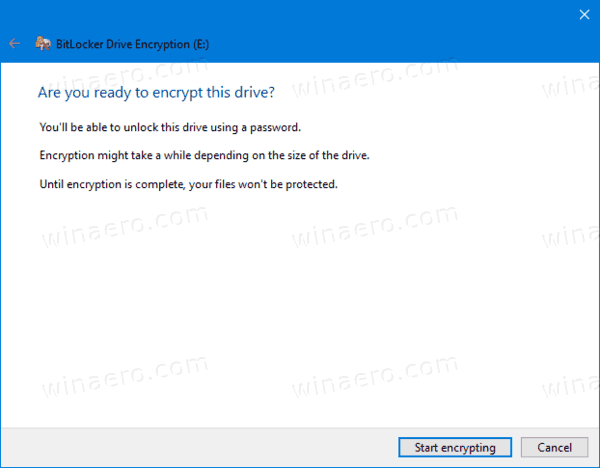
You are done. The fixed drive will be encrypted. This could take a long time to finish depending on the data size stored on the drive, and its capacity.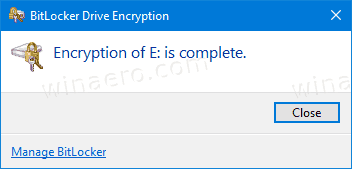
You can now check the BitLocker encryption status for the drive.
To Turn Off BitLocker for a Fixed Drive in Windows 10,
- Open File Explorer to the This PC folder.
- Right-click on the drive and select Manage BitLocker from the context menu.
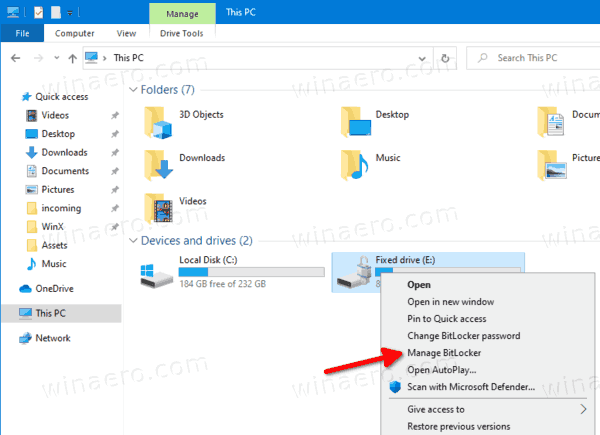
- Alternatively, click on Manage tab under Drive Tools in the Ribbon, then click on the Manage BitLocker command.

- Finally, you can open Control Panel\System and Security\BitLocker Drive Encryption.
- On the right side of the Drive Encryption Dialog, find your fixed drive, and click on the link Turn off BitLocker.
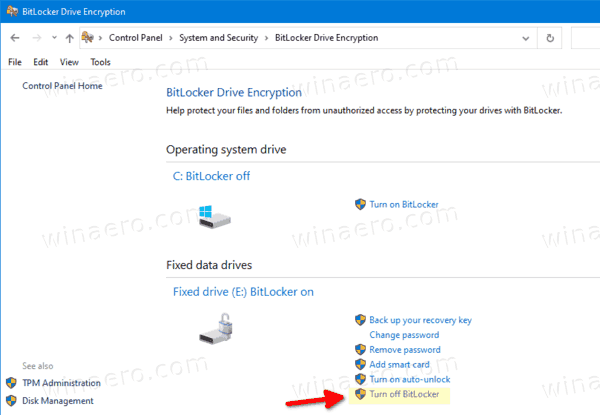
- Click on the Turn off BitLocker to confirm the operation.
You are done. BitLocker will decrypting the drive contents.
You can now check the BitLocker encryption status for the drive.
Also, you can disable BitLocker for an internal drive from Command Prompt or PowerShell.
To Turn Off BitLocker for a Fixed Drive from the Command Line
- Open a new command prompt as Administrator.
- Type and run the following command:
manage-bde -off <drive letter>:. - Substitute
<drive letter>with the actual drive letter of the drive you want to decrypt. For example:manage-bde -off D:.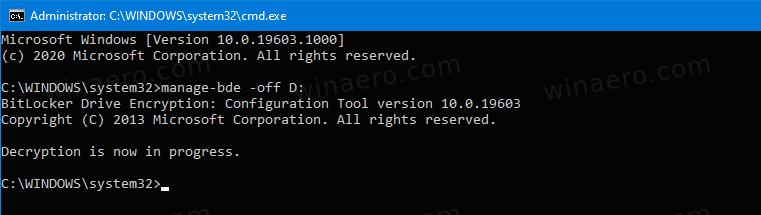
- Alternatively, open PowerShell as Administrator.
- Type and run the following command:
Disable-BitLocker -MountPoint "<drive letter>:". - Substitute
<drive letter>with the actual drive letter of the drive you want to decrypt. For example:Disable-BitLocker -MountPoint "D:".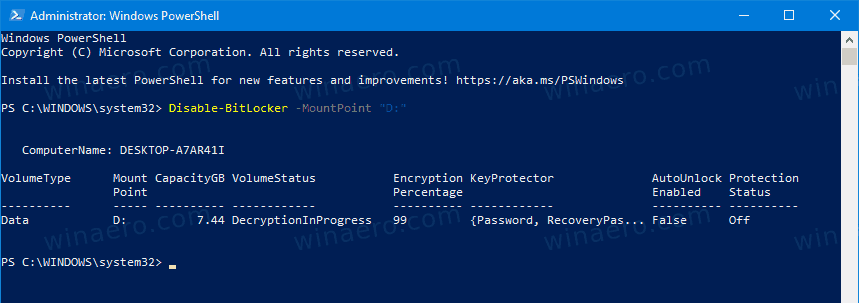
You are done!
Source: https://winaero.com/blog/turn-on-bitlocker-for-fixed-drives-in-windows-10/
'Access denied; you need (at least one of) the PROCESS privilege(s) for this operation' when trying to dump tablespaces
I am trying to backup mysql using the command
mysqldump -u root -p database_name > backup.sqlbut it is throwing an error:
'Access denied; you need (at least one of) the PROCESS privilege(s) for this operation' when trying to dump tablespaces
Also, i wanted to make a backup my database with all tables saperately sotored as a file. How can i do it?
Solution:
use --no-tablespaces
Sticky Password Review
Quick Summary
If every password is a key, I feel like a jailor. The weight of that huge keychain weighs me down more and more every day. It’s hard just to remember them all, but I’m also meant to make them hard to guess, different on every website, and change them all at least yearly! Sometimes I’m tempted just to use the same password for every website and be done with it! But that’s a very bad idea. Use a password manager instead.
Sticky Password is available for Windows, Mac, Android, and iOS, and works with a wide variety of web browsers. It automatically fills in online forms, generates strong passwords, and automatically logs you into the websites you visit. It’s less expensive than its main competitors yet the Windows app offers a similar number of features.
But there are some negatives. Unfortunately, the app looks a little dated, the Mac app is missing some important features, and the web interface offers little functionality. Why would you choose Sticky Password over its competitors? It offers two unique features that might appeal to you:
- Sync over a local network. If you’d rather not keep your passwords on the internet but still want them available on every device you own, Sticky Password is the best app for you. Its “no-cloud wifi sync” can synchronize your passwords between devices without storing them in the cloud. I’m not aware of any other app that can do this.
- Lifetime plan. If you’re sick of subscriptions and would rather just pay for the program outright, Sticky Passwords offers a Lifetime plan (see below). Buy it, and you’ll never pay again. It’s the only password manager I know of that offers this.
How much does it cost? For individuals, three plans are offered:
- Free plan. This offers all the features of the Premium plan to one person on one computer and includes a 30-day trial of Premium. It doesn’t include sync, backup and password sharing, so it won’t be a good long-term solution for most people, who own multiple devices.
- Premium plan ($29.99/year). This plan offers every feature and will sync your passwords to all of your devices.
- Lifetime plan ($199.99). Avoid subscriptions by purchasing the software outright. It’s equivalent to almost seven years of subscriptions, so you’ll have to use it long-term to make your money back.
- Plans are also available for Teams ($29.99/user/year) and Academics ($12.95/user/year).
New Update: Sticky Password kindly offers SoftwareHow readers an exclusive 50% off discount for both Premium and Lifetime plans, get this limited time offer here.
Buscar
Date of publication
Filter by category
Nuestros Partners
Search Post
About CNERIS
CNERIS is a company formed by young entrepreneurs from different sectors of the world of information. Our team consists of programmers, system administrators, graphic designers.



